CVE-2025-62722 - LinkAce - Stored XSS Vulnerability in Link Title Field Through Social Media Sharing Functionality
Author and Researcher

Ravindu Wickramasinghe
@rvz
Summary
The social media sharing functionality contains a Stored Cross-Site Scripting (XSS) vulnerability that allows any authenticated user to inject arbitrary JavaScript by creating a link with malicious HTML in the title field. When a user views the link details page and the shareable links are rendered, the malicious JavaScript executes in their browser. This vulnerability affects multiple sharing services and can be exploited to steal session cookies, perform actions on behalf of users, or deliver malware.
Details
The social media sharing functionality contains a Stored Cross-Site Scripting (XSS) vulnerability that allows any authenticated user to inject arbitrary JavaScript by creating a link with malicious HTML in the title field. When a user views the link details page and the shareable links are rendered, the malicious JavaScript executes in their browser. This vulnerability affects multiple sharing services and can be exploited to steal session cookies, perform actions on behalf of users, or deliver malware.
The vulnerability exists in the interaction between three components:
- Link Creation - The title field accepts arbitrary HTML without sanitization (
app/Http/Requests/Models/LinkStoreRequest.phplines 19-22) - Sharing Helper - The title is placed unencoded into share URLs (
app/Helper/Sharing.phpline 47) - Share Link View - The href attribute is rendered without escaping (
resources/views/models/links/partials/share-link.blade.phpline 1)
Vulnerable Code Flow
// app/Helper/Sharing.php - Lines 37-51protected static function generateLinkData(Link $link): array{ $subject = $link->title : trans(config('sharing.defaults.subject')); $shareText = trans(config('sharing.defaults.sharetext')); $shareText = str_replace('#URL#', $link->url, $shareText); return [ $link->url, self::encode($link->url), $subject, // subject - UNENCODED TITLE self::encode($subject), $shareText, self::encode($shareText), ];}Multiple sharing services in config/sharing.php use the #SUBJECT# placeholder (unencoded title) instead of #E-SUBJECT# (encoded title):
// Lines 41, 45, 73, 85, 97 - Examples of vulnerable services'reddit' = [ 'action' = http://www.reddit.com/submit?url=#URL#&title=#SUBJECT#',],'pinterest' = [ 'action' = http://pinterest.com/pin/create/button/?url=#URL#&description=#SUBJECT#',],'hackernews' = [ 'action' = https://news.ycombinator.com/submitlink?u=#URL#&t=#SUBJECT#',],'evernote' = [ 'action' = https://www.evernote.com/clip.action?url=#E-URL#&title=#SUBJECT#',],'tumblr' = [ 'action' = http://tumblr.com/share/link?url=#URL#&name=#SUBJECT#',],'flipboard' = [ 'action' = https://share.flipboard.com/bookmarklet/popout?v=#SUBJECT#&url=#E-URL#',],The resulting URL is then rendered in the view with unescaped output:
// resources/views/models/links/partials/share-link.blade.php - Line 1a href="{!! $href !!}" class="link-sharing {{ $class }}" title="{{ $title }}" target="_blank" rel="noreferrer nofollow"When a malicious title like "><img src=x onerror=alert(document.cookie)> is used, it breaks out of the href attribute and injects executable JavaScript. The payload executes when any user views the link details page where shareable links are displayed.
Affected pages include:
- Link detail view (
/links/{id}) - Link listing pages with sharing enabled (card and detailed views)
- Guest/public link views with sharing enabled
Proof of Concept
Steps to Reproduce
- Log in to LinkAce as any authenticated user
- Navigate to the link creation page at
/links/create - Enter a valid URL in the URL field (e.g.,
https://example.com) - In the title field, enter the following XSS payload:
"><img src=x onerror=alert(document.cookie)> - Save the link
- Navigate to the link details page by clicking on the newly created link
- Observe the shareable links section at the bottom of the page
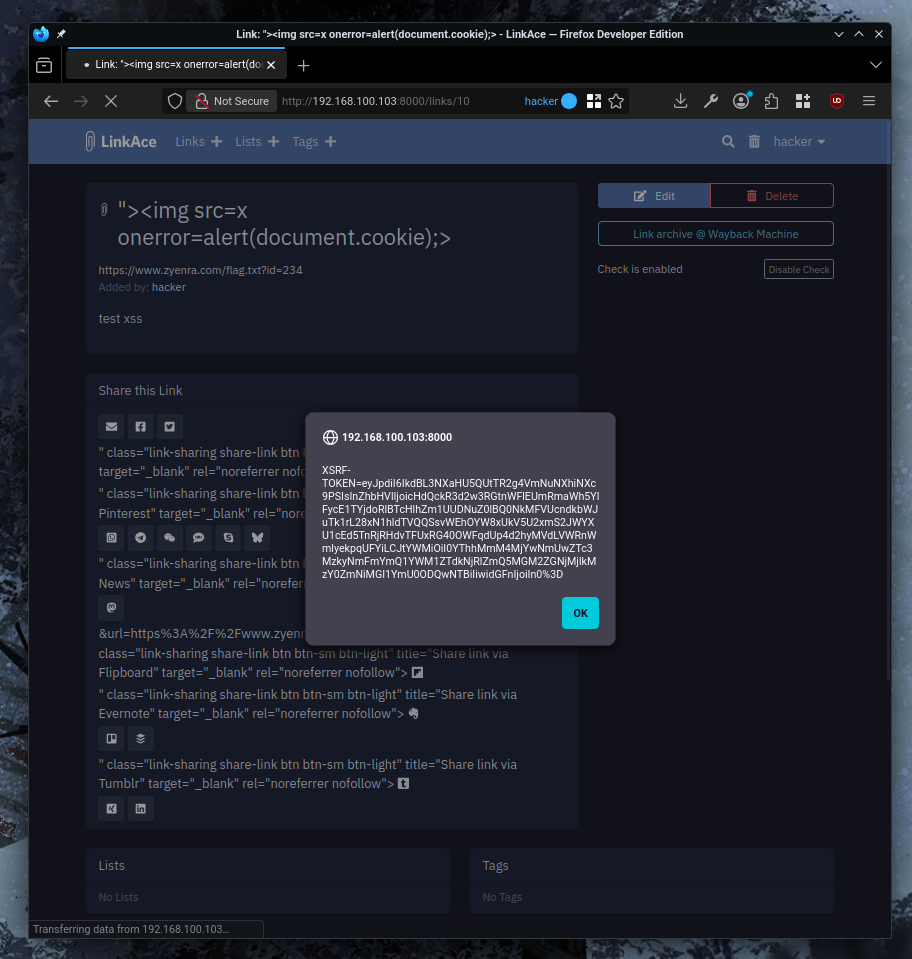
- The JavaScript payload executes immediately, displaying an alert with the session cookie
- Inspect the HTML source and observe that the malicious payload has broken out of the href attribute:
<a href="http://www.reddit.com/submit?url=https://example.com&title="><img src=x onerror=alert(document.cookie)>">
Proof of Concept (Video)
Proof of Concept (Image)
Recommendations
The vulnerability can be remediated by modifying the share link Blade template to properly escape HTML output. In the file resources/views/models/links/partials/share-link.blade.php at line 1, change the unescaped output syntax {!! $href !!} to the escaped syntax {{ $href }}. This ensures that any special HTML characters in the href attribute are converted to their HTML entity equivalents, preventing malicious payloads from breaking out of the attribute context and injecting executable code.
Laravel's Blade templating engine automatically applies htmlspecialchars() when using the {{ }} syntax, which encodes characters like quotes, angle brackets, and ampersands. This fix addresses the root cause of the vulnerability and applies universally to all sharing services configured in the application.
